Reading
Read Chapters 1-3, 4-5The Interrupt Vector Table
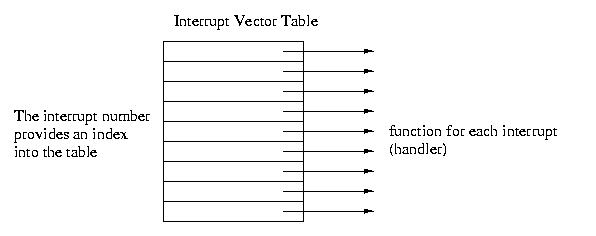
The interrupt vector table maps interrupts to the service routines that handle them. This table has one entry for each interrupt. Each entry contains the address of the handler. The interrupt number is used to index into the table. The address in this entry is dereferenced to execute the corresponding handler.
In a few machines the address of the interrupt vector table is fixed at 0. In most machines, it is stored in a register.

Direct Memory Access (DMA)
Direct memory access is an I/O mode that allows data to be transferred directly from an I/O device to a system's memory and vice-versa, with very little intervention from the system's main processor. Instead DMA capable devices rely on processors embedded within the devices themselves.
After intialization by the main processor, these devices take control of the bus and transfer the data directly into or out of the systems's memory. This leaves the main processor free to perform non-I/O related activity.
There is a trade-off, since the DMA-based device is in effect stealing the bus from the CPU. The CPU can not perform memory operations while the DMA transfer is occuring. Fortunately, most of what the CPU needs is stored internally within registers and caches, so DMA is usually a performance win.
Examples of DMA operations might include writing a 512 byte block to disk or a 1500 byte network packet. The device only needs to know the buffer address and the buffer length.
Often the devices have thier own buffers. But there is some electronics
required to interface with the devices. In the PC architecture, this is
handled by a separate chip on the motherboard.
Handling Protection
Protection involves many things including the following:
For now, we'll present a simple model for memeory protection. We'll
present a more sophisticated model later, but this one is sufficient for
aral OS to function
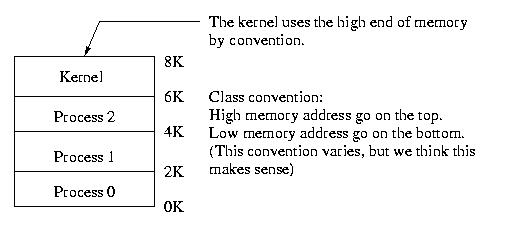
The goal is to make sure that, for example, process 2 can't go outside
of the 4K-6K region.
This requires hardware support -- we can't do it in software alone.
The simplest model is for us to add to registers: BASE and LIMIT. This is the simplest model, most computers are more complex.
In order to keep process 2 within it's 2K box, we can do one of two things:
Option #1:
Option #2:
Under the first scheme, the process must know the address range where it is running. Consider the difficulty for a language like C with pointers, char *At this point, do we have protection?
Not yet, we just have protection against accidents. malicious users cna just change the values of the BASE and LIMIT registers and then trample all over memory. To obtain true protection, we need more hardware support."Dual-Mode" Operation
To the best of our knowledge, this scheme doesn't have an official name. But your book calls it dual-mode operation, and this seems good enough to us.
Processors that support dual mode operation have two different modes:
For the moment, let's assume that we can get into and out of kernel mode at appropriate times. What instructions should be reserved for this mode? We'll call these privleged instructions.
There are three typical means of entering kernel mode. But they are all closely related:
Interupt: An interrupt can be used to switch into kernel mode, since both the table and the PSR are protected.
Exception: Instead of directly entering kernel mode via an interrupt, an alternative is to execute a privleged instruction This will generate a hardware exception. Typically, the kernel kills off the offending process: divide by 0, illegal memory address, &c. But the kernel knows what caused the execption and is free to implement its own policy. The exception handler can enforce this policy and allow the switch into protected mode.
Trap: A trap is a special kind of privleged instruction often called a "kernel call." Many machines actually only have one trap instruction. In these systems the paramters define the meaning of the trap.
Previously we gave you a simplified view of the interrupt vector table.
It is really an interrupt, exception, and trap table. It contains entries
for all three. Each interrupt, vector, or trap has a unique index into
the table.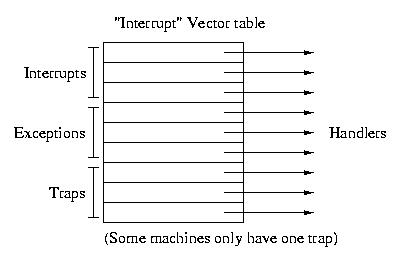
Student Question: Can you give an example of when a trap would
be called? Is it the responsibilty of the interrupt handler to return to
user mode?
Answer: Sure. Here's an example. And it is the responsiblility
for the trap to return to user mode on return form the trap.
main()
{
int fd;
fd = open ("fdo", 2);
write (fd, &buffer, len);
close (fd);
exit(0);
}Each of the above lines (except the fd declaration) results in a kernel call. Each generates a trap to get into the kernel.
For example, the library code for open might do the following:
PUSH foo and 2 onto the stackThe #3 is the parameter that tells the trap that the function is open. This code is implemented in the library instead of the program, because C doesn't have a trap instruction. The library is a tool for us to get this small amount of assembly into our programs.
TRAP #3
...
subroutine-like returnIn many ways, TRAP operates like a subroutine call. It saves state for return, including the PC, PSR, and other registers.
Student Question: Interrupt vs Trap. How strict are the names?
Answer: They are frequently misused. For example, the "Interrupt table" is really the "Interrupt, trap, and vector table." The names used are those used in assembly. These names are written by a software person, These writers aen't generally strict. For example, it really should be an interrupt, not a trap to enter kernel mode:
Interrupt: Asynchronous to the CPUStudent Question: How much state is saved by the hardware? We can't do it all in software, can we?
Exception: Something out of the ordinary
Trap: Invoked explicitly to cause a particular behavior
Answer: The hardware must save some things like the PC, the kernel
vs. user mode bit, &c. More might be saved in software or in hardware
depending on the OS. Saving any state information in software can be grueling
(Watch Prof. Johnson do acrobatics in front of the classroom as he explains
what it is like to try to move somewhere with nothing on which to stand.)
A Special I/O Device: The Timer Interrupt
The timer generates periodic interrupts at regular intervals -- "just like clockwork" (pardon a favorite pun). On most current machines it occurs every 10 ms or 100 times per second.
Why would we want this?
Answer: 10mS is a very long time in CPU time
Student Question: Are there any systems that have multiple clocks?
Answer: Many hardware engineers build multiple clocks into systems thinking that software people want it that way. Timer chips often have multiple clocks. But the OS typically uses only one of them. It is much simpler to generate interrupts at constant intervals and then time everything off of those in software.
Processes (Chapter 4)
What is a process? We've already started using these terms, so most of you have some idea about processes and programs.
One defintion is that a process is a program in execution.
A running program needs more than a file on disk, including hardware state:
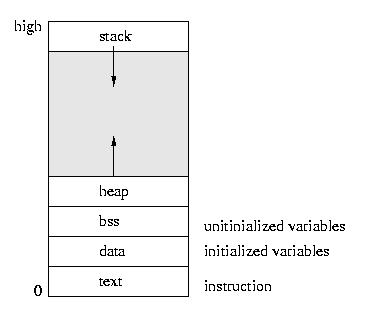
text, bss, data, heap, and stack are the UNIX terms for these parts
of a process context. The nomenclature may vary in other operating systems,
but is largely consistent.
Student Question: What happens if the stack and the heap overlap?
Answer: If you are luck, a very fast and bloody death. If you
are unluck the process suffers for a long time producing wrong results.